- Solutions
- Business Email Compromise
Assess the Impact of Business Email Compromises Fast
Find personal data & connect it to people quickly and accurate with Canopy’s Data Breach Response software.
Explore Canopy's AI-Powered PII Detection
Download our brochure to learn more.
See Canopy In Action
Canopy's Data Breach Response software leverages machine learning at every step, from PII detection through to generating a notification list.
Business email compromise (BEC), also called email account compromise (EAC), is the result of successfully phishing attempts that specifically target corporations and organizations rather than individuals. Cyber criminals impersonate trusted contacts, such as executives, coworkers, and vendors, to trick employees into clicking malicious links or providing sensitive information.
BECs are the second most common cause of cyber incidents and data breaches among SMEs. These attacks aren’t going anywhere — on the contrary, their frequency is steadily growing. The 2023 NetDiligence® Cyber Claims Study reported that the number of business email compromise claims increased by over 400% in the four-year period between 2018 and 2021.
Without the proper cyber protection or simply as the result of human error, BEC attacks can happen to any organization. They can result in cyber criminals gaining fraudulent payments or accessing confidential information if the compromised inbox has been used to send or receive unencrypted personal information (PI), personally identifiable information (PII), or protected health information (PHI). BECs can also serve as the point-of-entry for subsequent ransomware attacks.
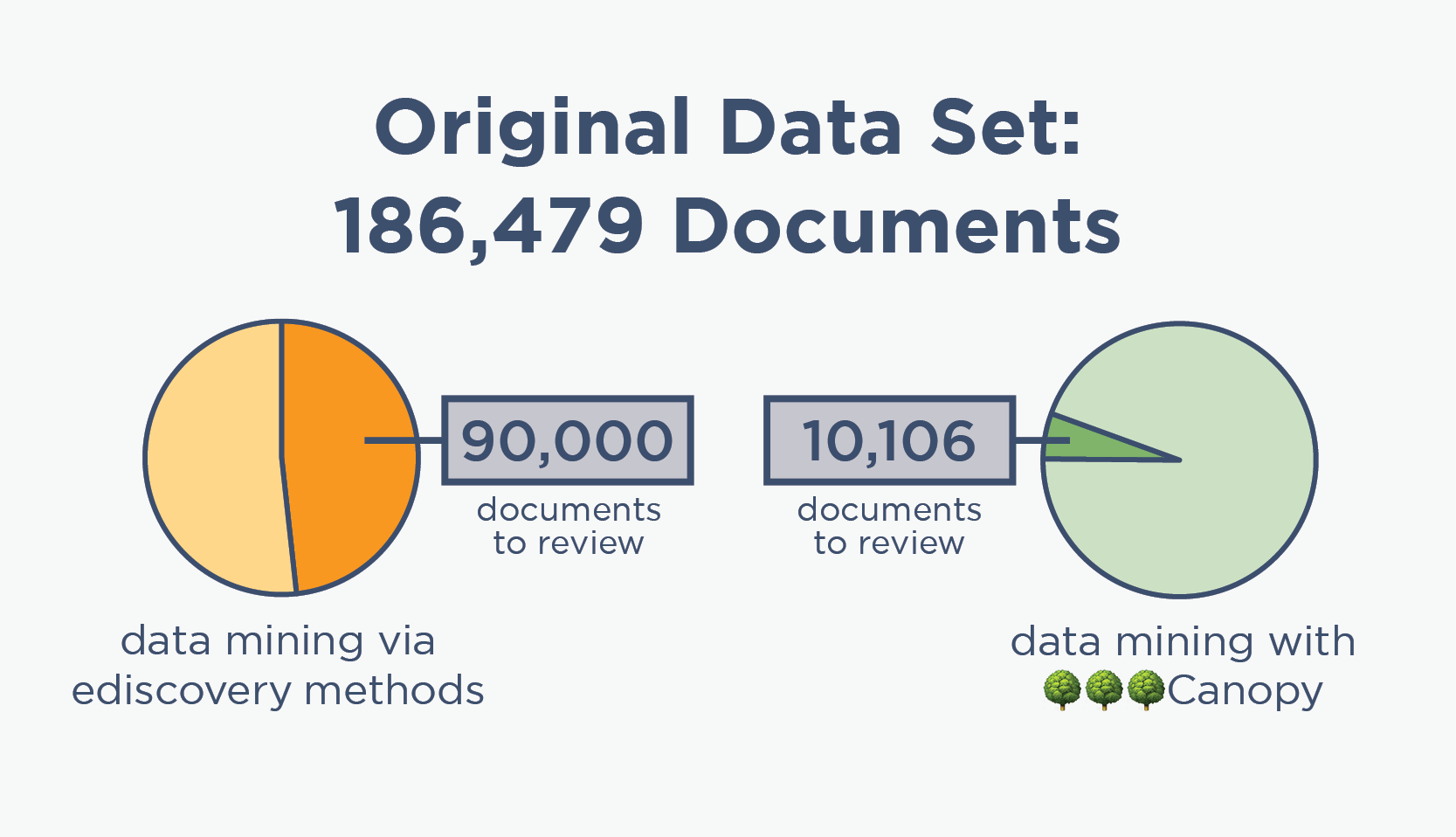
Data Mine PSTs Faster & More Accurately
Canopy’s Data Breach Response is the only software that is purpose-built for incident response data mining. Our patented AI streamlines the work of DFIR professionals and Review & Legal Service Providers, enabling them to zero in on personal data faster and more accurately than other tools.
Canopy's machine learning algorithms have detected tens of billions of PII elements and keep improving with every project. This powerful processing means that a single person can usually estimate scope and review cost in one day.
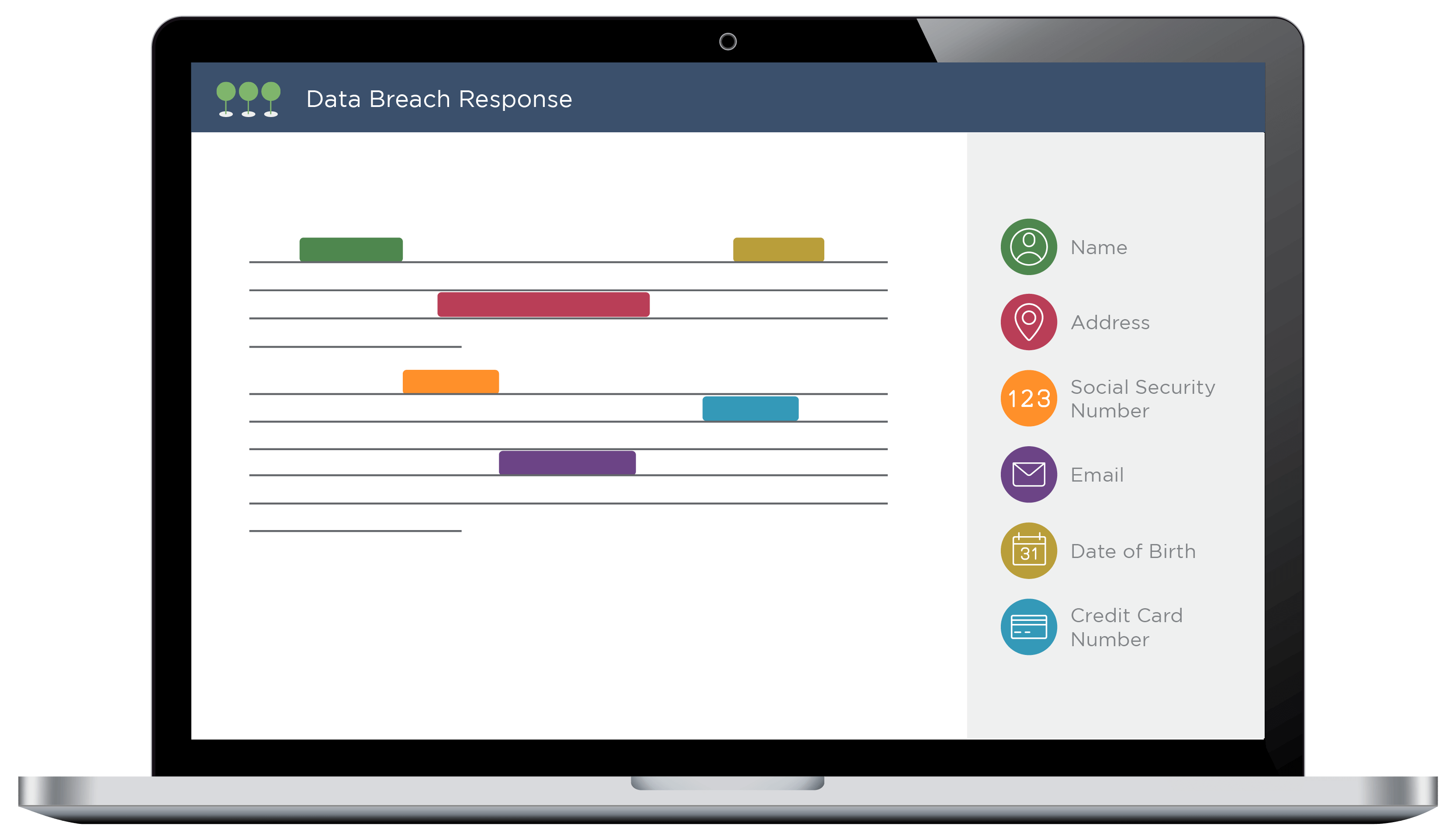
Leverage AI for More Streamlined Review
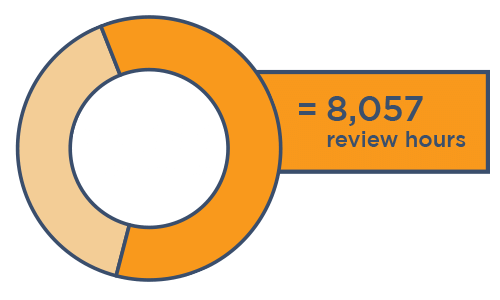
Canopy also saves review teams thousands of hours per project while simultaneously decreasing the risk of human and keystroke error.
The application clearly highlights detected PII in documents, enabling reviewers to quickly create profiles that connect people to data elements — all while maintaining links back to source documents. Our AI can even turn the process of linking PII to entities into an “accept or reject” workflow, eliminating the need to copy-and-paste data into spreadsheets.
All of these efficiencies add up to thousands or even millions of dollars saved per incident for organizations and their Cyber Insurers.
Save Big on Review Costs
"Canopy’s PII detection alone saved us thousands of review hours. Not only were we looking at less stuff, but we were looking at the right stuff."
🌳🌳🌳Canopy data mining

ediscovery data mining
Determine If a BEC Is a Breach
Not every ransomware attack results in a data breach. “Breach” is a determination that legal counsel makes after considering several factors, including what types of data were compromised, how many people were affected, and where those people live. If a breach is determined, compliance with jurisdiction- and sector-specific regulations can require strict deadlines.
Once PII detection and review are complete, Canopy makes entity consolidation a breeze. With AI-powered workflows, the application can automate most deduplication, then surface questionable records for human decision-making. This enables incident response teams to provide their clients’ law firms with the insights needed to make this determination much faster than with alternate tools. And if data breach notifications are required, Canopy’s streamlined creation of notification lists saves precious time.
Secure, Compliant Software
ISO 27001 Certification
We actively maintain an ISO 27001 certification and regularly conduct third-party penetration (pen) testing.
Data Security at Every Step
Data is encrypted at rest and in transit. It resides in a virtual private cloud (VPC) within your jurisdiction.
Granular Admin Control
Tenant admins can set user permissions for everything from accessing data to exporting entity lists.
Software that’s Purpose-Built for BEC
Download our white paper, The Inflated Cost of Data Breach Response (And How We Got Here), to see the difference Canopy makes for claims costs.
If you’re an incident response provider, request your personalized demo to see how you can deliver faster, more accurate incident response data mining services with Canopy’s AI-powered software.