- Solutions
- Law Firms & Legal Counsel
Assess breach compliance needs faster.
Canopy Partners provide fast, accurate data breach response so that you can advise your clients quickly & save them money.
Explore Canopy's AI-Powered PII Detection
Download our brochure to learn more.
See Canopy In Action
Canopy's Data Breach Response software leverages machine learning at every step, from PII detection through to generating a notification list.
After an organization discovers that a cyber incident has occurred, one of the first calls they make is to legal counsel. Executives want to immediately understand their regulatory risk so that they can implement a breach response strategy, including notifying the right authorities and people.
In order to advise their clients, data privacy attorneys need to quickly find out how many people were affected and what personally identifiable information (PII) or protected health information (PHI) was compromised. Both the amount of sensitive data and the threat of cyber risks are continuously growing, making it harder to get these answers quickly and within a reasonable budget. This is causing progressive law firms to rethink their approach and their technology.
AI-Powered PII Detection Delivers Faster Insights
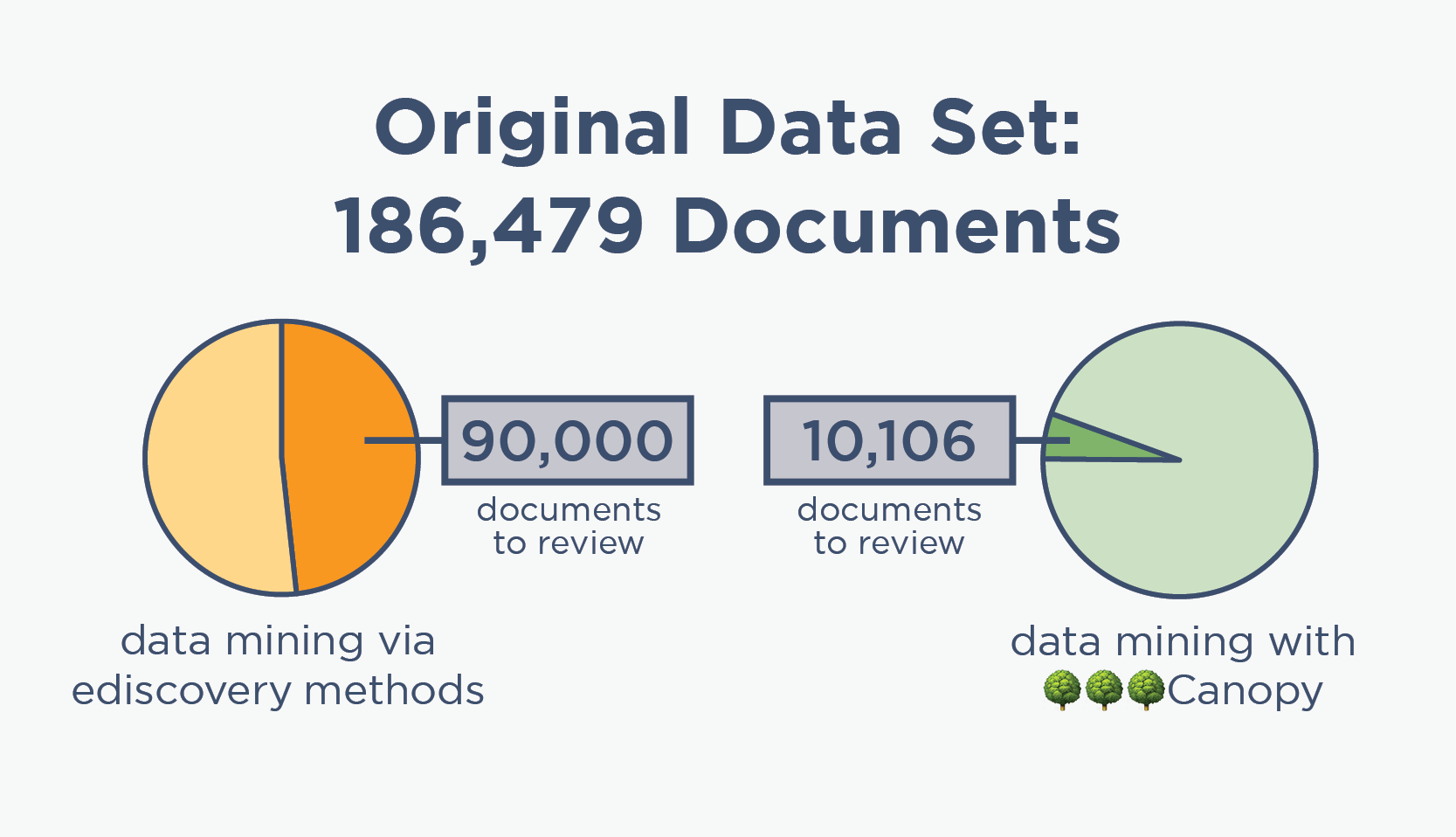
In data breach cases, attorneys won't know the true scope until humans have reviewed all potentially-sensitive documents. But many data mining methods are vastly over-inclusive at finding PII/PHI, resulting in thousands of wasted hours reviewing documents that aren't sensitive.
Canopy's Data Breach Response software is backed by hundreds of machine learning models. Our partners can zero in on PII/PHI with precision and help you understand the scope of a breach much faster.
Data Breach Response ≠ Ediscovery
Until recently, cyber and data privacy lawyers have relied on ediscovery processes and software to handle data breach response. These sectors seem similar at 30,000 feet: data needs to be normalized, then culled down, then reviewed by humans before getting to the final deliverable.
But at ground level, their differences are clear. Because ediscovery tools were not made for finding PII/PHI in compromised data, they are over-inclusive, leading to huge numbers of irrelevant documents being manually reviewed. This time-consuming task not only makes it difficult to meet breach notification deadlines, it also makes breach response significantly more expensive.
By using a Canopy Partner for data mining & PII review, you can ultimately deliver better services and save your clients money.
ediscovery data mining
🌳🌳🌳Canopy data mining
Better PII Detection Lowers Clients' Overall Costs
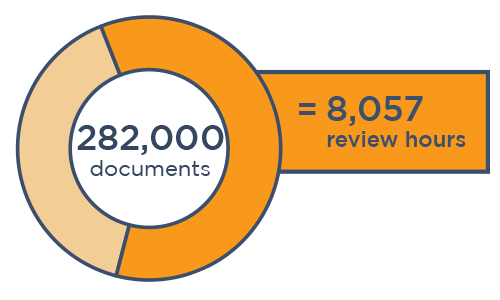
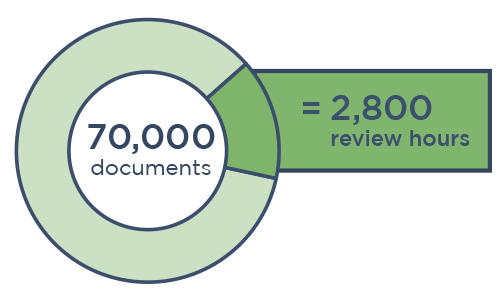
When it comes to data breach response, data mining isn't the most time-consuming part — the subsequent human review is. When reviewers look at more documents than necessary to find PII in compromised data, it can take thousands more hours for legal counsel to get the insights it needs.
Download our case study to see how one Canopy partner completed its PII review in nearly one-third the time (saving its client over $300,000) using our Data Breach Response software.
Secure, Compliant Software
ISO 27001 Certification
We actively maintain an ISO 27001 certification and regularly conduct third-party penetration (pen) testing.
Data Security at Every Step
Data is encrypted at rest and in transit. It resides in a virtual private cloud (VPC) within your jurisdiction.
Granular Admin Control
Tenant admins can set user permissions for everything from accessing data to exporting entity lists.
Defensible Data Mining with AI
The definition of individual sensitive data classifications is consistent, making PII/PHI detection a perfect match for artificial intelligence.
Each of Canopy’s hundreds of machine learning models has a specific focus (like social security number, credit card number, religious affiliation, or diagnostic code) and is trained with thousands or even millions of examples. The application’s classifications are then validated by humans as part of the review process, helping its algorithms continuously improve. Canopy's AI has already detected billions of PII/PHI elements, with more added continuously.
Choose Partners that Save Your Clients Money
When it comes to breach response and notification, there's no time (or money) to waste.
Canopy has a network of partners across the globe that are trained on our Data Breach Response software. Their ability to target PII/PHI with precision means that you get faster insights and your clients save hundreds of thousands — or even millions — of dollars on their total project cost.