The global business community has been frenzied this week after hackers exploited a flaw in MOVEit, allowing them to access the data of hundreds of organizations in the United States. Compromised data includes the driver’s licenses and state ID cards of millions of people in Louisiana and Oregon, and the attack also affected multiple U.S. federal agencies. As MOVEit is a trusted file-transfer software, it’s likely that even more sensitive personal data was exposed.
The MOVEit hack highlights the vulnerabilities that exist in even the most sophisticated software, reminding us that data breaches are often a matter of “when, not if.” This attack is alleged to have been conducted by Clop, a ransomware gang based in Russia.
Now that the vulnerability is patched, the hundreds of affected organizations have an immediate need to assess the compromised data. They need to know as soon as possible whether they've experienced a legally defined breach and, if so, what people and personal data were affected. Their timeline isn’t just dictated by regulations — with the whole world watching, the reputational stakes are high.
Canopy Makes Data Mining Faster & Easier
Canopy’s patented Data Breach Response software is the world’s first and only tool purpose-built for incident response data mining. With its speed and precision, it is the best choice for determining whether an incident is a breach quickly and meeting tight notification deadlines without sacrificing quality.
Canopy uses advanced AI to streamline data mining at every step:
Process
Hundreds of machine learning algorithms are continuously trained to detect PII/PHI in any data set, from emails and text documents to spreadsheets, PDFs, and many other file types.
Assess
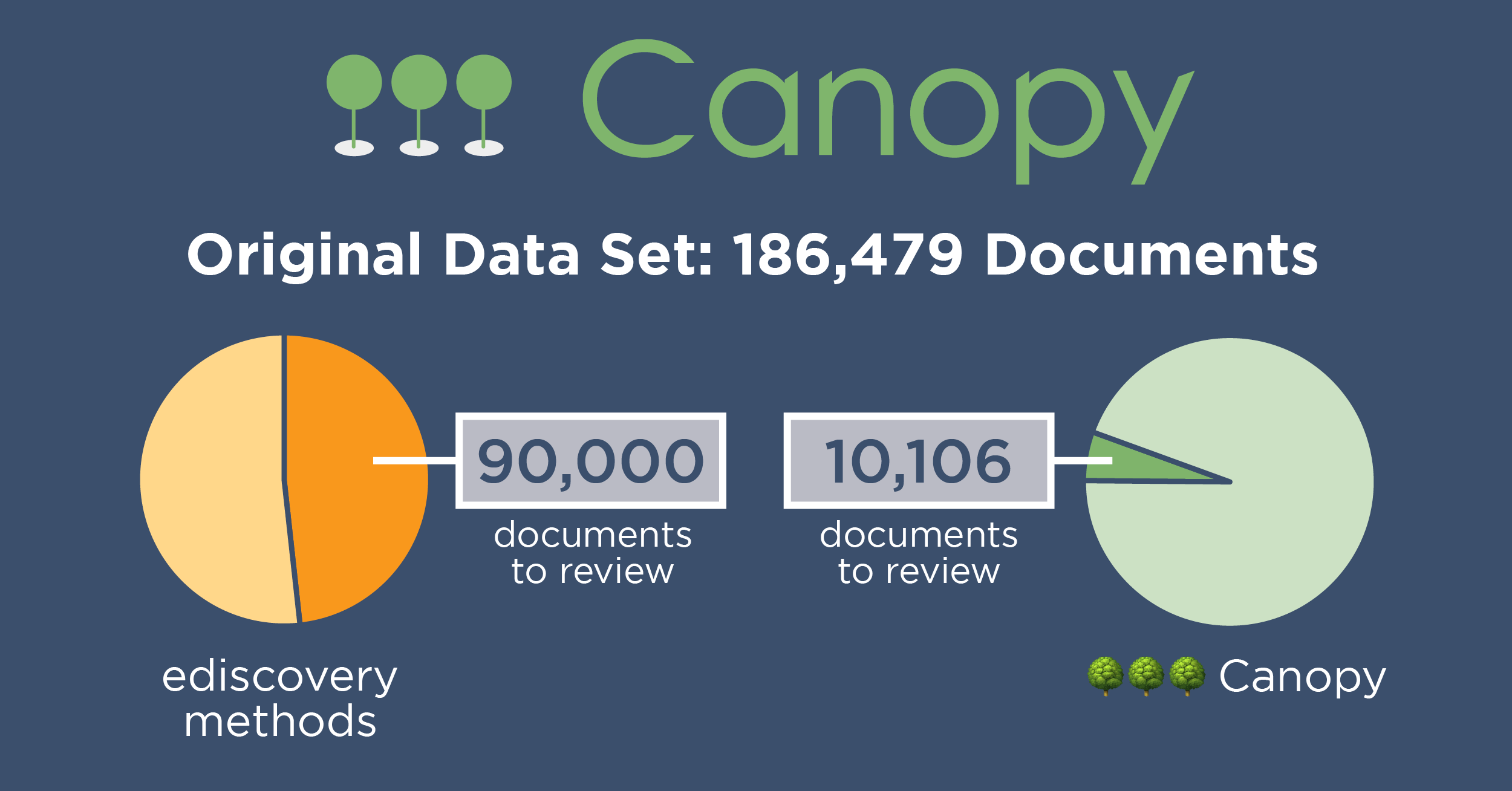
Canopy largely automates PII/PHI detection, eliminating the need for iterative regex (regular expressions) and keyword searches. This means a single person can typically estimate the project scope on Day 1 — and the results will be more accurate, too.
Review
Canopy helps reviewers work much faster while simultaneously decreasing the risk of human & keystroke error. It turns the process of linking PII and people into a simple “accept or reject” workflow, eliminating the need to copy and paste data into spreadsheets or other programs.
Consolidate
Canopy’s advanced entity management functionality takes the heavy lifting out of entity resolution, deduplicating entity lists with a few clicks. This removes the need to manually locate and match repeated references to the same person throughout a data set.
With Canopy, DFIR teams and Review & Legal Service Providers can tell their clients whether they’re dealing with a data breach faster than with other tools. And if a breach is determined, Canopy allows them to deliver the fastest, most accurate data mining services.
Canopy Isn't Just Faster – It's Better for Insurers, Too
With its speed and precision, Canopy is the best choice for cyber insurance data mining panel providers. Our streamlined workflow enables more automation, which means less human effort and lower costs.
Canopy uses hundreds of machine learning models, each trained to identify a different personal data element. This powerful PII detection eliminates the need for iterative, tedious regex and keyword searches. It’s more accurate than those, too, allowing for incident response teams to zero in on sensitive documents.
Human review is necessary in data mining, and it’s often the most expensive part. Canopy’s improved PII detection accuracy means humans need to look at fewer documents to find the same amount of sensitive data. Further, our AI streamlines the process of linking PII to people and tracking source documents, speeding up reviewers’ work. Finally, deduplicating the list of affected people — a task that takes multiple people and hours of work in other tools — can be done in just a few clicks.
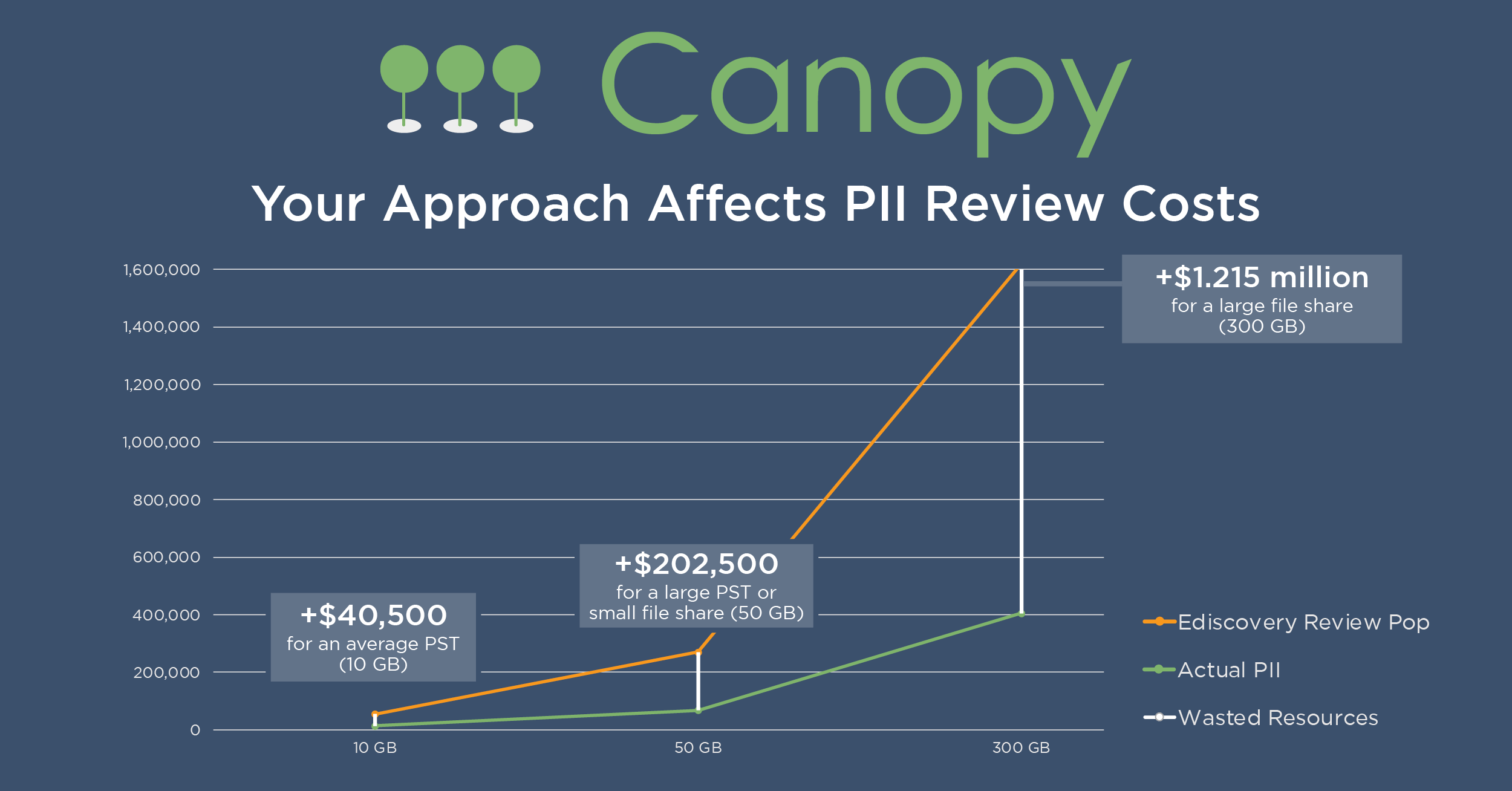
All of these efficiencies add up to thousands or even millions of dollars saved on a single data breach claim.
Our team is ready to help you provide improved data mining services to your clients in the wake of the MOVEit hack. Contact us to learn more, or request your demo today.