It's Time to Rethink Your Approach to Data Breach Response
Improve accuracy and meet notification deadlines faster with Canopy's AI-powered software.
Purpose-Built for Every Phase
When a cybersecurity event occurs, incident response teams must race the clock to determine whether it is legally considered a breach. Was personally identifiable information (PII) or protected health information (PHI) compromised? If so, they could be bound by strict, non-negotiable notification deadlines enforced by GDPR, HIPAA, FERPA, and other data privacy regulations — or risk consequences like fines and damage to their reputation.
Powered by AI and machine learning, Canopy’s patented Data Breach Response software reduces the time, cost, risk, and effort associated with the defensible detection of sensitive data. Here’s how it streamlines data breach response at every step:
Download Canopy's Guide to Effective Data Breach Response
Review all 5 phases of data breach response in more detail, and see how Canopy speeds up the process every step of the way.
Download Canopy PII Detection Brochure
Learn about Canopy's powerful processing and data mining capabilities, scan supported PII types, and preview its Impact Assessment Report.
Download Case Study
See how Canopy saved one review team 2,000 hours compared to ediscovery methods with improved data mining and advanced PII detection.
Download Case Study
See how Canopy consolidated 4.28 billion entities to 3 million unique people with machine learning-powered deduplication.
Request a Demo
See how Canopy's Data Breach Response software leverages machine learning at every step, from PII detection through to generating a notification list.
Download White Paper
Trying to use ediscovery for data breach response? Explore 5 reasons why ediscovery isn't the right choice — and don't miss #3: It's a Different Kind of Review.
Watch Webinar
Hear Adi Elliott, CRO at Canopy, discuss why ediscovery tools and processes are not the right choice for data breach response.
Download Canopy's PII Detection Brochure
Learn how our advanced PII detection works.
PHASE ONE
Process
Canopy’s hundreds of machine learning algorithms are continuously trained to detect PII/PHI in any data set, from emails and text documents to spreadsheets, PDFs, and many other file types.
Whether your data is structured or unstructured, the software immediately scans it, unpacks and categorizes the files, and classifies the PII — no prior data normalization necessary. In fact, we recommend that you avoid normalizing the data and leave the heavy lifting to us.
Canopy often completes processing within hours, then generates an automatic Impact Assessment Report that provides an overview of the data set, including the types and quantities of found PII elements and which documents contain them.
PHASE TWO
Assess
Say goodbye to data mining via endless rounds of regex and keyword searches. Instead, harness Canopy’s AI-powered processing to get to the PII in your data faster.
Thanks to the processing Canopy does in phase one, you’ll have all of the insights you need to immediately begin assessing the project scope. Our PII detection and filtering capabilities make it easy to flag sensitive documents for review and ignore the rest, and advanced functionality like our gallery view enables you to move even faster.
Because Canopy eliminates the need for iterative search, a single person can typically estimate the project scope and review cost on the same day they begin their assessment — and the results will be more accurate, too.
PHASE THREE
Review
Canopy helps teams work significantly faster through PII Review while simultaneously decreasing the risk of human & keystroke error.
Our software uses machine learning to make it both fast and easy for reviewers to link the PII detected in your data to people. PII is clearly highlighted as reviewers click through documents, enabling them to quickly create entity profiles for individuals and connect them to breached data elements — all while maintaining links back to source documents.
As Canopy learns about a specific project, its AI turns the process of linking PII to entities into a simple “accept or reject” workflow, eliminating the need to copy-and-paste data into spreadsheets.
PHASE FOUR
Consolidate
Forget about spreadsheets and SQL — our Data Breach Response software's advanced entity management functionality takes the heavy lifting out of entity resolution.
In addition to automatically deduplicating identical people within an entity list, Canopy also suggests merging entities when one individual is referred to in varying ways throughout the data, as might be seen with nicknames, abbreviated names, or maiden names.
This entity management functionality saves response teams significant time by removing the need to manually locate and match repeated references to the same person throughout a data set.
PHASE FIVE
Notify
The ultimate deliverable of any data breach response project is a deduplicated list of unique affected individuals and their compromised PII.
Canopy consolidates all of this information as reviewers work so that the entity list is ready to export as soon as the review is complete.
And because certain jurisdictions and industries have specific notification requirements, Canopy provides export options to meet your unique needs.
Battle-Tested & Proven Technology
Canopy’s Data Breach Response software has been used on hundreds of incidents, and its algorithms have identified tens of billions of PII/PHI elements. The software is in active use worldwide on projects of all types and sizes — from standard business email compromises (BECs) to multi-terabyte ransomed file shares, and everything in between.
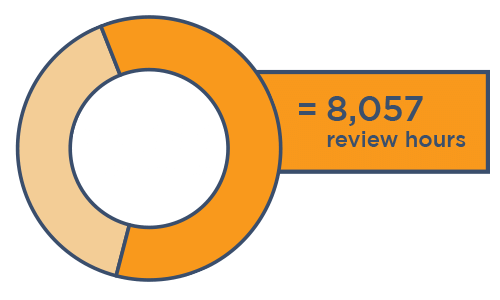
"Canopy’s PII detection alone saved us thousands of review hours. Not only were we looking at less stuff, but we were looking at the right stuff."
🌳🌳🌳Canopy data mining

ediscovery data mining
Software that Meets Everyone's Needs
From the review and response teams to the affected individuals, there are many people involved anytime a security incident occurs. Canopy's Data Breach Response software benefits them all:
Digital Forensics and Incident Response (DFIR) Teams
Data mining done in hours — find PII, PHI, and high-risk data faster than any other software on the market.
Review & Legal Service Providers
Connect PII to people with ease, so you can deliver faster results & win more projects.
Law Firms & Legal Counsel
Our Partners provide fast, accurate data breach response so that you can advise your clients quickly & save them money.
Cyber Insurance Companies
Save millions per year when your digital forensics panel providers use Canopy’s Data Breach Response software.
Ready to speed up your data breach response?
Download Canopy's Guide to Effective Data Breach Response for a more detailed look at this process, or request your personalized demo to see how our AI-powered solution can transform your workflow.